
In the United States, more than 1.3 billion data-breach victim notices were issued in 2024, a scale indicator that shows how widely breaches ripple through customers and employees (it’s not a 1:1 count of unique victims). Globally, the average cost of a data breach was about $4.4 million in 2025, underscoring how expensive security failures have become. Behind every serious defense against these escalating threats stands a Chief Information Security Officer (CISO), a C-suite executive whose role has expanded from managing controls to driving risk decisions at the highest levels.
The modern CISO operates where cybersecurity intersects with business strategy, regulatory pressure, and operational resilience. This guide explores the eight critical roles and responsibilities that define modern CISO leadership, useful for aspiring security executives, current CISOs, and leaders who want more return from their security investment.
What is a Chief Information Security Officer (CISO)?
A Chief Information Security Officer (CISO) is a senior executive responsible for developing, implementing, and managing an organization’s information security program. This C-suite role encompasses protecting organizational data, systems, and technology infrastructure while enabling business objectives through secure innovation.
The CISO role is widely traced to the mid-1990s, when Citicorp (later part of Citigroup) appointed Steve Katz as the first Chief Information Security Officer in 1995. Since then, the role has evolved dramatically from technical roots into a position that bridges cybersecurity, business strategy, and organizational leadership.
Recent data reveals that 82% of CISOs report directly to the CEO. This evolution reflects growing recognition that security is a fundamental business risk requiring board-level visibility.
The CISO differs from other technology leaders: while the CIO focuses on IT strategy and the CTO on technological innovation, the CISO focuses on security, risk management, and compliance. According to Glassdoor data, the median CISO salary is $317,098 annually, underscoring the critical role of the CISO.
Why is the CISO Role Critical?
Speed matters in a breach because the longer an attacker stays inside, the more damage they can do. IBM’s 2025 research shows the average breach lifecycle fell to 241 days in 2025, down from 258 days in 2024 (from identification to containment). That’s progress, but “months-long” is still the reality, and it’s exactly why organizations need a CISO who can shorten detection-to-containment with the right priorities, controls, and response muscle.
Accountability is also a problem because the likelihood of consequences for attackers is low. The World Economic Forum estimates that the likelihood that a cybercrime entity is detected, successfully investigated, and prosecuted in the U.S. is around 0.05%. In plain terms: you can’t rely on enforcement to protect you. Your defense has to hold.
When breaches do occur, confusion worsens outcomes. A survey cited by Varonis found 64% of Americans don’t know what steps to take in the event of a data breach. That human uncertainty inside and outside the company raises the bar for CISO leadership: clear incident playbooks, fast decisions, and communication that keeps people from becoming the second wave of the incident.
For organizations navigating this landscape, Cybersecurity Training has become essential for survival and growth.
8 Roles and Responsibilities of Chief Information Security Officer
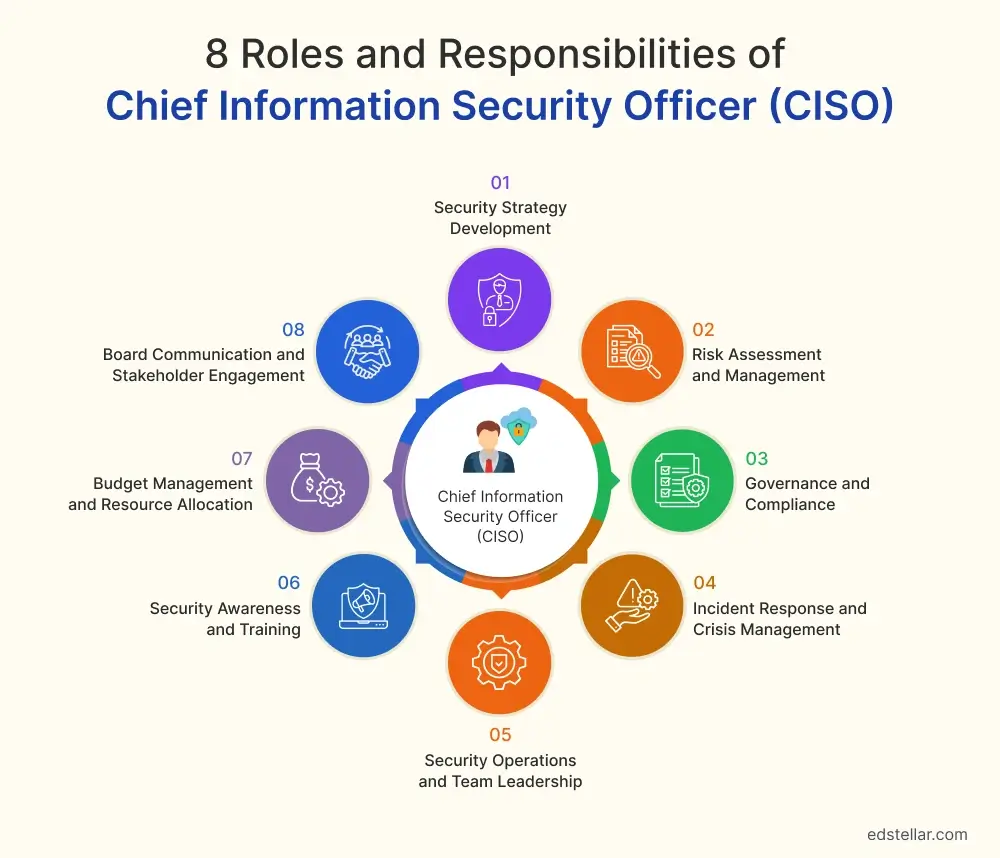
1: Security Strategy Development
The CISO’s foremost responsibility is to craft and execute comprehensive security strategies that protect organizational assets while enabling business objectives. This requires balancing security and usability, innovation and risk mitigation, and immediate tactical needs with long-term strategic positioning.
Developing an effective security strategy begins with understanding the organization’s business model, competitive landscape, risk appetite, and strategic objectives. The most effective CISOs position security as a business enabler rather than a constraint. The security strategy encompasses vision, multi-year roadmaps, technology architecture decisions, and measurable objectives aligned with business outcomes.
Strategic CISOs champion “security by design” approaches in which security considerations inform system architecture from inception. They establish security standards for cloud deployments, application development, network segmentation, identity management, data protection, and endpoint security.
When security demonstrably drives business success, CISOs gain executive support and budget approval, which are essential for building robust security programs.
2: Risk Assessment and Management
Risk assessment and management form the cornerstone of effective security leadership. The CISO must continuously identify, evaluate, prioritize, and mitigate risks threatening organizational assets and operations.
The process begins with comprehensive asset identification and valuation, followed by threat modeling that examines potential attack vectors and adversary capabilities. Vulnerability assessment through automated scanning, manual testing, and architecture reviews identifies weaknesses across the technology estate.
Risk quantification translates technical vulnerabilities into business terms: rather than reporting “critical vulnerabilities discovered,” effective CISOs articulate “Unmitigated vulnerabilities create $X million exposure to fraud losses, regulatory penalties, and reputation damage.”
The CISO employs frameworks like the NIST Cybersecurity Framework and ISO 27001 to ensure comprehensive risk practices. Third-party risk management has become increasingly critical as supply chain attacks pose a growing threat. Risk mitigation strategies include risk avoidance, reduction, transfer, and acceptance, with the CISO recommending appropriate strategies and securing leadership approval.
Organizations can strengthen capabilities through Cybersecurity Risk Management Training and Risk Leadership Training.
3: Governance and Compliance
Security governance and compliance establish policies, standards, procedures, and controls governing how organizations protect information and meet regulatory obligations. The CISO develops comprehensive security policies covering acceptable use, access control, data classification, incident response, and vendor management.
Security standards translate policies into specific technical requirements for system configurations, encryption, authentication, network segmentation, and secure development. Procedures provide step-by-step instructions ensuring consistent security practices organization-wide.
Compliance management navigates data protection regulations, including GDPR, CCPA, HIPAA, and sector-specific requirements. Industry frameworks such as PCI DSS, FISMA, and SOX add layers. The CISO manages relationships with auditors and regulators, prepares evidence, and implements corrective actions.
Governance, Risk, and Compliance (GRC) programs integrate these activities into cohesive frameworks. Security certifications like ISO 27001, SOC 2, and FedRAMP demonstrate compliance to customers and partners.
Organizations benefit from Security Policy Management Training for practical policy development skills.
4: Incident Response and Crisis Management
Incident response represents the CISO’s most visible responsibility. When security incidents occur, the CISO must lead coordinated responses that contain damage, restore operations, fulfill legal obligations, and maintain stakeholder confidence.
Preparation forms the foundation. The CISO develops comprehensive incident response plans defining roles, escalation procedures, communication protocols, and technical responses. Regular testing through tabletop exercises ensures team readiness.
The Security Operations Center (SOC) provides 24/7 monitoring and rapid incident identification. Detection and analysis determine whether suspicious activity constitutes genuine incidents. Containment strategies limit impact while preserving evidence. Eradication removes threat actor presence and remediates vulnerabilities. Recovery restores normal operations while ensuring threats haven’t maintained hidden access.
Crisis communication requires careful coordination with legal, PR, and executive leadership. SEC rules require public company disclosures within four business days, according to CSO Online. Post-incident analysis transforms incidents into learning opportunities.
Business continuity and disaster recovery planning extend crisis responsibilities. Organizations with tested DR plans reduce breach recovery costs by an average of $2.66 million.
5: Security Operations and Team Leadership
The CISO must excel as a leader who builds, develops, and directs high-performing security teams. Modern security organizations comprise specialized functions: security operations, engineering, architecture, governance/risk/compliance, and application security.
Talent acquisition faces challenges given the persistent global skills shortage. The CISO develops creative recruitment strategies, including university partnerships, internal training programs, and managed service providers. Team development requires continuous learning through training, conferences, certifications, and hands-on experience with new technologies.
Cross-functional collaboration extends influence beyond the security organization. The CISO builds relationships with IT, development, business units, legal, HR, and executive leadership. Security culture building represents perhaps the most impactful responsibility; organizations with strong security cultures consistently outperform those where security remains solely the security team’s concern.
According to ISACA, 48% of security teams report directly to the CISO, with this structure correlating with better business alignment. Organizations benefit from People Management Training to develop security leadership.
6: Security Awareness and Training
Human error is the top cybersecurity risk, with phishing accounting for 30% of incidents, according to IBM. The CISO transforms employees from vulnerabilities into the first line of defense through comprehensive awareness programs.
Programs begin with new-employee security onboarding, covering passwords, phishing recognition, data handling, and incident reporting. Annual awareness training maintains knowledge using interactive scenarios and real-world examples. Role-based training addresses different security risks across roles: developers need secure coding, finance needs fraud detection, and executives need awareness of business email compromise.
Phishing simulation programs provide hands-on learning. Organizations running regular simulations see click rates decline from 30-40% to under 5%. Security champion networks extend the CISO’s reach by identifying security-minded employees who serve as local advocates.
Measuring effectiveness goes beyond completion rates to assess knowledge retention, behavior change, and risk reduction using metrics such as phishing results, incident rates, and security metrics.
Organizations accelerate programs through Cybersecurity Training solutions.
7: Budget Management and Resource Allocation
Financial stewardship requires the CISO to develop realistic budgets, justify security investments, and demonstrate ROI. Budget development accounts for technology costs, personnel expenses, professional services, compliance costs, and cybersecurity insurance.
Gartner estimates that organizations spend an average of 5.6% of their IT budgets on security and risk management.
Justifying investments requires translating security into business terms and financial impact. Return on security investment (ROSI) frameworks quantify security value by calculating expected loss reduction versus control costs.
Resource allocation requires strategic prioritization, focusing resources on the highest-priority risks. Build versus buy decisions significantly impact budgets and effectiveness. The CISO evaluates whether to develop custom capabilities or purchase commercial products based on total cost, deployment time, maintenance, and strategic alignment.
Measuring and communicating program value strengthens budget positions. The CISO tracks incidents prevented, vulnerabilities remediated, and compliance achievements, translating technical metrics into business outcomes.
8: Board Communication and Stakeholder Engagement
Modern CISOs interact with boards on a near-continuous basis, providing security insights that inform strategic decisions. Effective board communication requires translating technical concepts into business language, with a focus on risk, financial exposure, regulatory compliance, and strategic enablement.
Board reporting covers risk landscape briefings, organizational risk profiles, incident updates, program effectiveness, and strategic initiatives. Visual communication proves particularly effective using data visualizations, risk heat maps, and executive dashboards.
SEC rules now require public companies to disclose material cybersecurity incidents within four business days and provide annual cybersecurity reports. Building credibility requires consistency, transparency, and realistic communication.
Stakeholder engagement extends to C-suite relationships. Each requires tailored communication: CEO (business enablement, strategic risk); CFO (security ROI, budget optimization); COO (operational resilience); CIO (technology alignment); General Counsel (regulatory compliance, legal liability).
Essential Skills and Qualifications for CISOs
The CISO role demands a rare combination of technical expertise, business acumen, leadership, and interpersonal skills. Deep technical knowledge forms the foundation, typically developed through progressive security roles spanning operations, engineering, architecture, and management.
Professional Certifications:
- CISSP (Certified Information Systems Security Professional)
- CISM (Certified Information Security Manager)
- CCISO (Certified Chief Information Security Officer)
- CRISC (Certified in Risk and Information Systems Control)
Education: Most CISOs hold bachelor’s degrees in computer science or IT. Increasingly, CISOs pursue graduate education, including MBAs, to develop competencies in business strategy and organizational leadership.
Experience: CISO roles require 10-15+ years of progressive security experience through paths like: Security Analyst → Engineer → Architect → Manager → Director → CISO.
Critical Competencies:
- Business and financial acumen
- Leadership and people management
- Communication and influence across audiences
- Emotional intelligence
- Continuous learning mindset
- Crisis management and decision-making
Conclusion
The Chief Information Security Officer occupies one of the most critical executive roles in modern organizations. The eight core responsibilities, security strategy development, risk management, governance and compliance, incident response, team leadership, security awareness, budget management, and board communication, demonstrate the multidimensional nature of CISO leadership requiring technical expertise, business acumen, leadership capabilities, and communication effectiveness.
As cyber threats evolve, digital transformation accelerates, and regulatory requirements expand, the CISO’s strategic importance will continue to grow. Organizations that invest in CISO leadership, provide appropriate authority and resources, and foster a security-conscious culture will outperform competitors and build resilience.
For aspiring CISOs, success requires continuous learning, practical experience, business competency development, and the cultivation of communication skills. For current CISOs, effectiveness depends on evolving toward a strategic business partnership, demonstrating security value, building high-performing teams, and enabling organizational objectives. For organizations, maximizing security investment requires creating conditions in which security leadership thrives through executive support, adequate resources, and realistic expectations.
Take Action: Strengthen Your Security Leadership
For Organizations:
- Assess current CISO support and security maturity
- Invest in security team training and development
- Foster security culture from the top
- Explore Cybersecurity Training Solutions
For Security Professionals:
- Develop strategic skills beyond technical expertise
- Pursue Cybersecurity Risk Management Training
- Build leadership through Risk Leadership Training
For Executive Leadership:
- Empower your CISO with authority and resources
- Strengthen board oversight of security
- Invest in Leadership Development Programs
The future belongs to organizations that treat cybersecurity as a strategic advantage, invest in security leadership capabilities, and build resilient cultures where security enables innovation and growth.
Additional insights at Top 10 Must-Have Skills for Cybersecurity Experts.
Ready to strengthen your security posture? Contact Edstellar to discuss customized cybersecurity training solutions and leadership development programs.
Continue Reading
Explore High-impact instructor-led training for your teams.
#On-site #Virtual #GroupTraining #Customized

Bridge the Gap Between Learning & Performance
Turn Your Training Programs Into Revenue Drivers.
Schedule a ConsultationEdstellar Training Catalog
Explore 2000+ industry ready instructor-led training programs.

Coaching that Unlocks Potential
Create dynamic leaders and cohesive teams. Learn more now!

Want to evaluate your team’s skill gaps?
Do a quick Skill gap analysis with Edstellar’s Free Skill Matrix tool

Transform Your L&D Strategy Today
Unlock premium resources, tools, and frameworks designed for HR and learning professionals. Our L&D Hub gives you everything needed to elevate your organization's training approach.
Access L&D Hub Resources.svg)
.svg)



.svg)



.svg)
.svg)
.svg)
.svg)

